A Github repository contains useful information on clean code practices as well as code examples. Not all of the principles outlined here must be strictly followed. These are only recommendations.
References
A Github repository contains useful information on clean code practices as well as code examples. Not all of the principles outlined here must be strictly followed. These are only recommendations.
References
Running a.NET application in a variety of environments can make collecting diagnostic artifacts (e.g., logs, traces, and process dumps) difficult. A dotnet monitor is a tool that provides a unified way to collect these diagnostic artifacts whether you’re running on your desktop machine or in a Kubernetes cluster.
dotnet monitor exposes an HTTP API to query available processes, collect diagnostics artifacts, and check on the status of the requested artifacts
To understand how much memory a process is using, we can keep an eye on its various memory counters.
Private Memory: This is the amount of RAM that has been allocated to the process privately. In general, “Private memory” does not include any memory used by the process’s shared DLL files.
Virtual Memory: represents the process’s total virtual address space.
Working Set: This is the portion of “Virtual memory” that is currently resident in RAM and can be accessed without causing a page fault.
[Read More]An IPv4 address consists of 32 bits. Each string of numbers separated by the period consists of 8 bits, represented by 0 to 255 in numerical forms.
CIDR is a group of IP addresses that are allocated to the customer when they demand a fixed number of IP addresses. When compared to classful addressing, there is no waste of IP addresses in CIDR because only the number of IP addresses requested by the customer is allocated.
[Read More]A TLS handshake occurs when a user navigates to a website over HTTPS and the browser first begins to query the website’s origin server. A TLS handshake occurs whenever any other HTTPS communication occurs, including API calls. The steps are summarized in the diagram below.

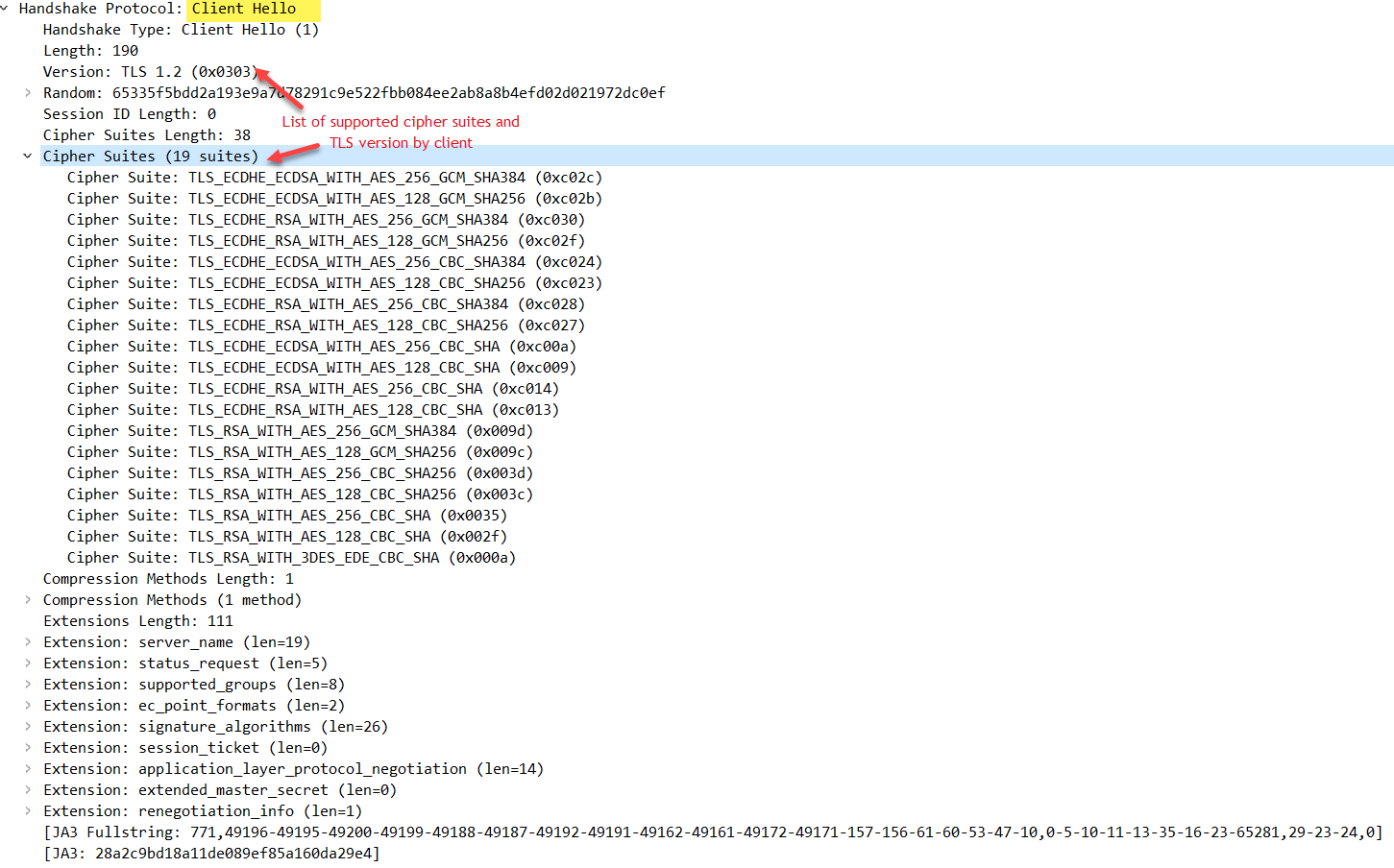
Client Hello
The client indicates the SSL/TLS and cipher suite versions that it supports.
Server Hello
The server sends the client a message containing the SSL/TLS version and cipher suite it has chosen. The server then transmits the TLS certificate, public key, and signature.
[Read More]