A TLS handshake occurs when a user navigates to a website over HTTPS and the browser first begins to query the website’s origin server. A TLS handshake occurs whenever any other HTTPS communication occurs, including API calls. The steps are summarized in the diagram below.

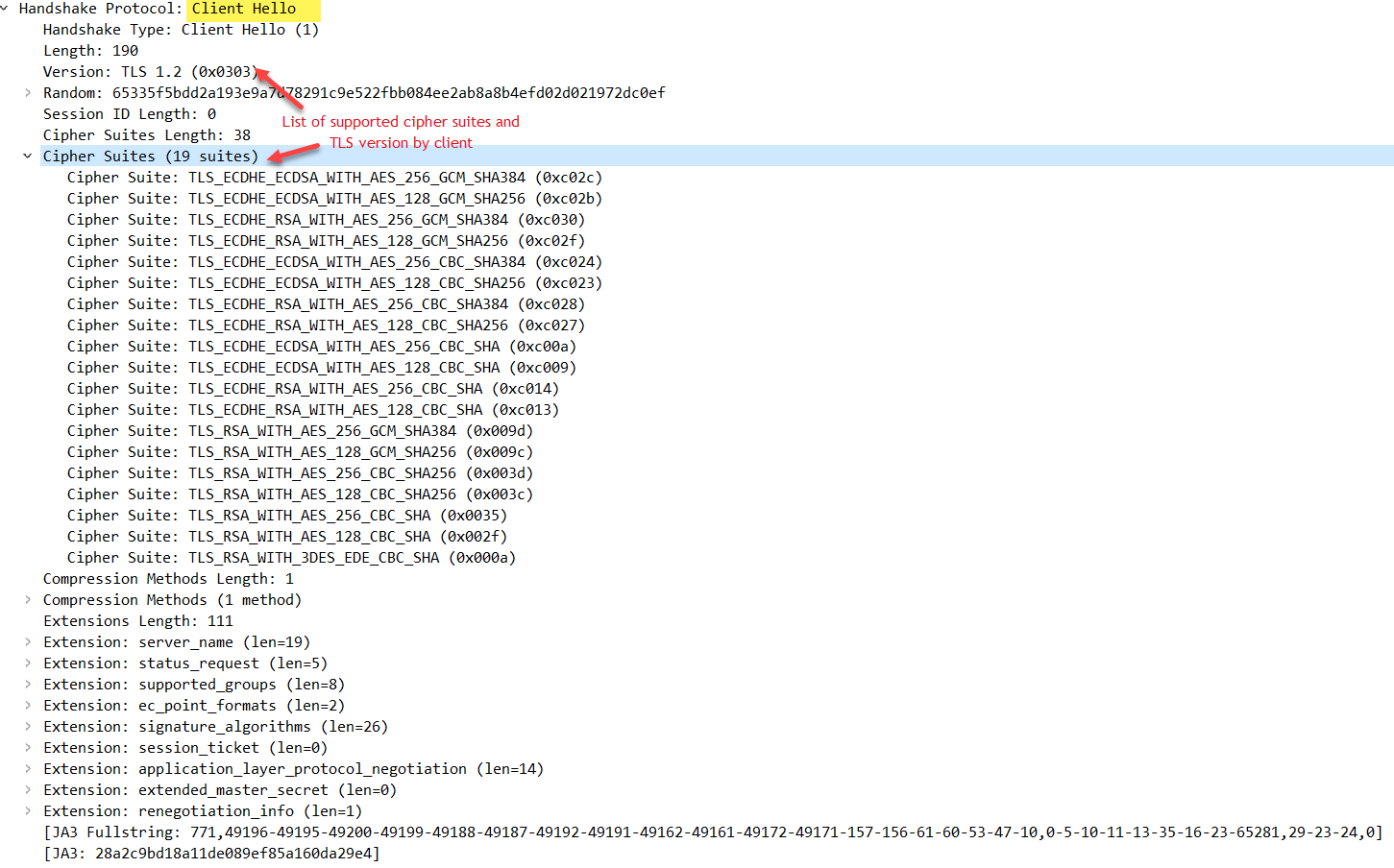
Client Hello
The client indicates the SSL/TLS and cipher suite versions that it supports.
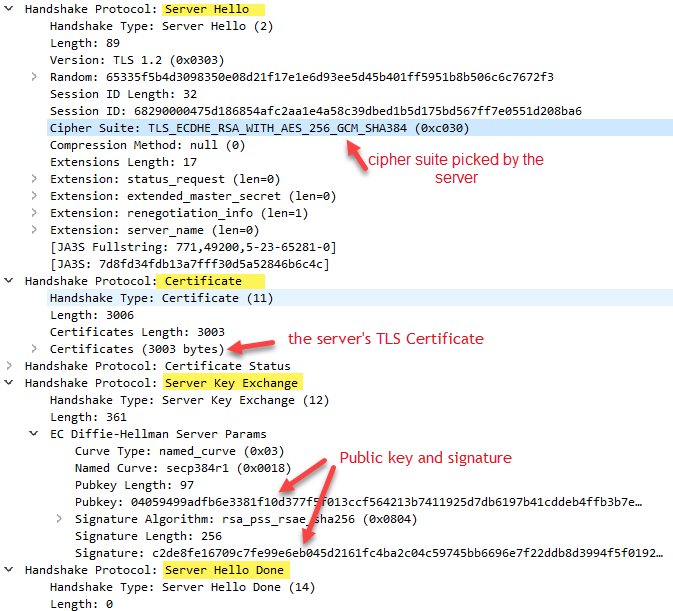
Server Hello
The server sends the client a message containing the SSL/TLS version and cipher suite it has chosen. The server then transmits the TLS certificate, public key, and signature.
Client key Exchange
The client generates a random session key (also known as the pre-master key). Encrypt the session key with the public key of the server. The encrypted session key is sent to the server. Only the server’s private key can be used to decrypt the session key after it has been encrypted. The session key can only be known by the client and server because only the server has the private key.
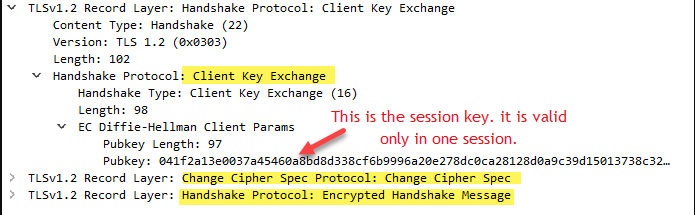
Change Cipher Spec
The client and server send the change cipher spec message to notify the receiving party that subsequent records will be protected by the just-negotiated CipherSpec and keys.
Encrypted Handshake
The client and server encrypt HTTP traffic with the session key.
This completes the TLS v1.2 protocol handshake process.
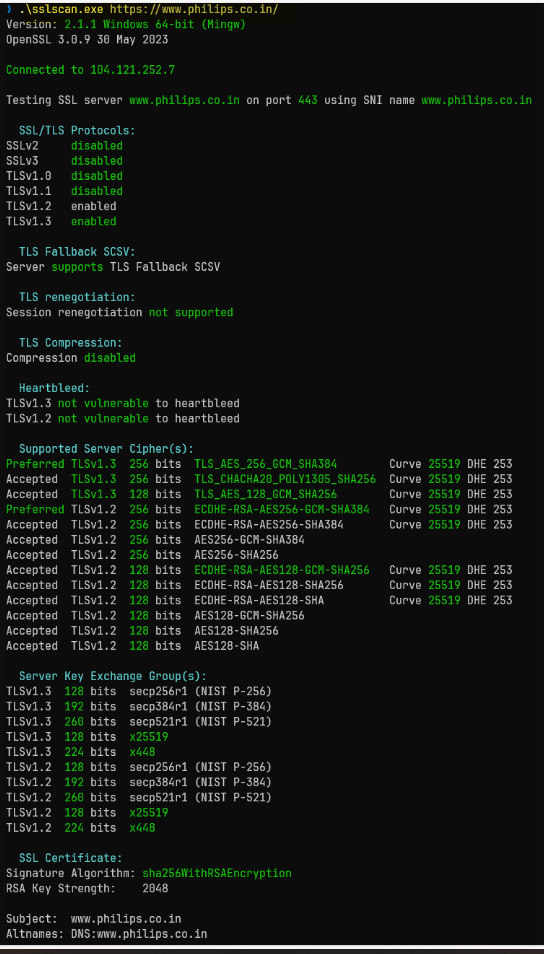
SSL Scan tool
There is a handy tool for testing SSL-enabled services and discovering supported cipher suites. The tool is available in the github repository.
References